What is Stealth VPN Protocol and How Does it Work?
To protect your VPN connection from censors, Stealth employs obfuscation. The goal is to make VPN traffic appear as regular HTTPS connections or “normal” communication. Stealth accomplishes this by tunneling obfuscated TLS via TCP. This differs from most widely used VPN protocols that typically employ UDP, which is simpler to identify and block.
Even if your government tries to control access, you’ll be able to get through complex VPN blocks, access censored websites, and interact with people on social media.
#Quick Summary
- The goal of Stealth VPN Protocol is to make VPN traffic appear as regular HTTPS connections or “normal” communication to bypass VPN blocks.
- Stealth Protocol is a secure protocol. It adds a new security layer to the current protocol to ensure the tightness of the security measures.
- Why you should use Stealth VPN?
- If you’d prefer to hide your personal information from your internet service provider.
- You can bypass the restricted websites.
- You can access the network at normal speed without throttling
Read more for further details about how does the Stealth VPN Protocol work and why you should use it.
What is Stealth VPN Protocol?
A “Stealth VPN” is a VPN server or protocol that can pass off VPN traffic as regular web traffic, even while your network administrator or firewall is doing a thorough packet inspection. It is made to be difficult to detect by firewalls and programs that are meant to hinder VPN traffic.
The Stealth VPN protocol is highly optimized for performance along with these obfuscation techniques. Stealth can perform better than prior obfuscated VPN protocols, typically developed on top of OpenVPN.
Stealth VPN protocol can get beyond most firewalls and VPN blocking techniques. Check the below video for better understanding of what is stealth vpn protocol:
[Read more: Wireguard vs OpenVPN: Key Differences Between the Two Protocols]
What is Obfuscated VPN and How Does VPN Obfuscation Work?
Obfuscated VPNs are VPN servers that are designed to mask the traffic they generate to bypass network filters and censorship mechanisms. They aim to conceal the content and destination of the traffic to make it difficult to detect and block.
These servers use various techniques to obfuscate the traffic they generate, such as encrypting the data, disguising the protocol used for communication, and mimicking legitimate traffic patterns to avoid detection.
Obfuscated VPNs are often used by individuals or organizations that operate in countries with strict internet censorship laws or by people who are concerned about their online privacy and security. Obfuscated servers are especially useful if you worry that your government is tracking you. In addition, if a university or school bans VPN usage, obfuscation can be used to hide the fact that a VPN is being used.
Why Should You Use a Stealth VPN Protocol?
Stealth VPN technology is a must-have for some individuals or businesses. If you are in a nation where internet access has stringent regulations, it could be very difficult to access some websites without a VPN service with stealth capabilities.
There are many reasons why you should use the stealth protocol; here, we’ve listed a few key reasons:
1. Data Privacy
Stealth/Obfuscated VPN services are a wonderful choice if you’d prefer to hide your personal information from your internet service provider. Your VPN traffic will be mingled with the daily transmission of billions of other HTTPS data packets, and your ISP won’t know what’s happening.
As more nations are considering the ideas like forbidding encryption or restricting VPN use, this Stealth protocol technique is gaining more traction these days.
2. Unblock websites
Also, the network administrator might restrict VPN access. So you can bypass the restriction if your VPN traffic is disguised (obfuscated) as standard SSL traffic.
3. Bypass Firewall
Firewalls that prevent VPN traffic are frequently used in states that regulate internet access. Stealth protocol crosses the barrier of the firewall easily by disguising the traffic.
4. Ensures your ISP doesn’t throttle
Some firewalls won’t stop the VPN traffic but will significantly slow it down. Sometimes ISPs throttle specific network traffic, like peer-to-peer file-sharing protocols. Even large ISPs, such as mobile service providers, throttle VPN traffic. By using stealth protocol, you can access the network at normal speed.
5. Access Streaming Platforms that Forbid VPN Use
Most streaming Platforms are putting a lot of effort into blocking VPN usage on their platforms. You can escape the VPN blocking and access the streaming websites through obfuscation.
[Read more: What Is Wave Browser – Should You Remove It?]
Is Stealth Protocol Secure?
Modern symmetric communication protocols encrypt and decrypt their whole transmission of data and messages using a single secret key, which gives scope for security threats.
Stealth uses a pseudo-random number generator for the symmetric-key cryptographic technique, which increases the security of contemporary communication. It first generates four shared secret keys using an algorithm to encrypt the message.
To make it very difficult to circumvent the security protocol, Stealth alters its private keys with each communication. Stealth protocol never replaces the existing protocol or the authentication mechanism; it just adds a new security layer to the current protocol to ensure the tightness of the security measures.
How Does a Stealth Protocol Work?
The basic function of a Stealth protocol is to mask VPN data packets as ordinary HTTPS traffic. Even the most restrictive firewalls won’t try to block HTTPS packets because they are necessary for transmitting secure data like passwords and details over the internet. This is why stealth VPN technology works so well.
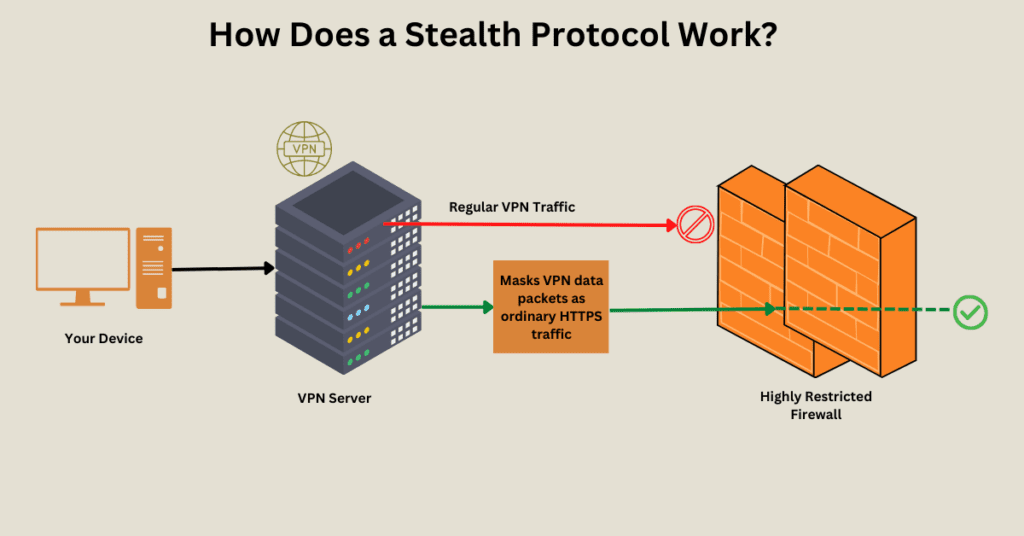
1. Removes the Meta Data from Packet Header
Typically, an OpenVPN data packet has two components:
The header contains information about packet identification and routing. Whereas the payload of the encrypted data packet will forward to the appropriate web address.
The header of a packet contains details that can be used to pinpoint its source and the port number. Additionally, it contains details designating the packet as OpenVPN data. A stealth VPN eliminates all the meta information from a packet header of the VPN protocol using a method known as “Obfuscation.”
It’s like deleting the official identity record of a person. So you need to find out about his nationality. Similarly, if you’ve removed the meta information from the packet header, you can’t identify the data packet’s source.
[Read more: How to Fix MacBook Screen Flickering?]
2. Disguised as Standard HTTPS Encrypted Web Traffic
After obscuring the data packet’s source, it is disguised as normal HTTPS encrypted web traffic by following the process below.
Stealth VPN applies the second layer of encryption, either SSL or TLS, to the OpenVPN data packet and allocates the data to port 443. It is the port that HTTPS communication normally uses. This makes the data packet almost impossible to prevent and practically indistinguishable from the conventional https traffic of any common website.
How to Choose the Best Stealth VPN?
Choosing the best stealth VPN can be a complex process, as there are many factors to consider. Here are some of the most important factors to consider when choosing a stealth VPN provider:
- Obfuscation: One crucial feature of a stealth VPN is obfuscation. This technology disguises your VPN traffic as regular internet traffic, making it harder for network administrators or government agencies to identify and block your VPN usage. Look for a VPN provider that offers advanced obfuscation techniques to bypass deep packet inspection (DPI) and other forms of VPN detection.
- Encryption strength: It is important to choose a VPN provider that offers strong encryption to keep your online activities private and secure. Look for providers that offer encryption standards such as AES-256.
- No-log policy: A good stealth VPN provider should have a no-log policy, which means they do not keep records of your online activities. This helps to ensure that your privacy is protected even if the VPN provider is subpoenaed or hacked.
- Multiple Hop: Another feature to consider is the option for multiple hop connections. This means your VPN traffic is routed through multiple servers in different locations, adding an extra layer of anonymity and making it more challenging to trace your online activities back to your original IP address.
- Network size and speed: A large network of servers with high-speed connections is important for ensuring a fast and reliable VPN connection.
- Cost: VPN providers offer a range of pricing plans, so it is important to find one that fits within your budget.
- Compatibility: Make sure that the VPN provider you choose is compatible with the devices and operating systems that you use.
- Customer support: Good customer support is important for getting help and resolving any issues that may arise. Look for a VPN provider that offers 24/7 support and multiple support channels such as email, live chat, and phone.
6 Best Stealth VPNs to Bypass Firewall
1. NordVPN

NordVPN’s obfuscated servers help bypass VPN restrictions by disguising VPN traffic as regular traffic. Connect by switching to the OpenVPN protocol, selecting “Obfuscated” from the Specialty Servers list, and choosing a location if desired.
2. VyprVPN

VyprVPN’s Chameleon technology employs unmodified OpenVPN protocol to enable users to bypass restrictive networks set by governments, corporations, and ISPs for an open internet experience while retaining the proven security of OpenVPN.
3. Surfshark

Surfshark’s Camouflage mode or Obfuscation feature removes VPN traces from your connection to make it appear as a regular internet connection, enhancing security without compromising it. Surfshark’s stealth VPN conceals VPN usage by encrypting the VPN data to resemble normal internet traffic.
4. CyberGhost

CyberGhost prioritizes privacy and operates NoSpy servers in their headquarters. In addition to top-of-the-line encryption protocols (WireGuard, OpenVPN, IKEv2), they offer features like split tunneling, a kill switch, and DNS/IP leak protection to enhance privacy and keep connections stealthy.
5. Proton VPN

Over the years, Proton VPN has developed technologies like Secure Core VPN, alternative routing, and VPN Accelerator to enhance privacy and connection speeds. As many governments have increased their efforts to block VPNs, Proton VPN has introduced Stealth, a protocol designed from scratch to make VPN connections almost undetectable. Protonvpn Stealth Protocol is available on all plans, including the Free plan, to promote online freedom. Currently, it can be used on Android, macOS, and iOS apps. However, sometimes users might face the Protonvpn not connecting issue due to the scheduled maintenance of the ProtonVPN servers.
6. ExpressVPN

ExpressVPN’s “stealth VPN” feature uses obfuscation technology to disguise VPN traffic as regular browsing, making it undetectable by deep packet inspection. This feature is useful for unblocking Netflix and bypassing online censorship. The stealth servers automatically activate when deep packet inspection is detected, without the user’s knowledge, making VPN usage completely invisible.
Here is a table comparing some of the best stealth VPN providers based on the factors mentioned above:
| Provider | Encryption | No-Log Policy | Speed | Compatibility | Price |
|---|---|---|---|---|---|
| 1. NordVPN | AES-256 | Yes | Super Fast | Android, iOS, macOS, Windows, Linux | Moderate |
| 2. VyprVPN | AES-256 | Yes | Average | iOS, macOS, Windows, Android, Android TV, Apple TV | Moderate |
| 3. Surfshark | AES-256 | Yes | Super Fast | Android, iOS, Windows, macOS, ChromeOS, Linux | Moderate |
| 4. CyberGhost | AES-256 | Yes | Average | Android, iOS, macOS, Windows, Linux | Moderate |
| 5. ExpressVPN | AES-256 | Yes | Fast | Android, iOS, macOS, Windows, ChromeOS, Linux | Expensive |
Stealth VPN Vs Wireguard VPN
Stealth VPN and WireGuard are both Virtual Private Network (VPN) technologies that offer users secure and private internet access. However, they are some key differences between the two protocols.
WireGuard is considered more secure, faster, and easier to configure than Stealth VPN. However, Stealth VPN is compatible with a wide range of devices and operating systems, while WireGuard is only supported on a limited number of platforms. Additionally, WireGuard is designed to minimize logging, while Stealth VPN may keep some connection logs.
| Feature | Stealth VPN | WireGuard |
|---|---|---|
| Protocol | OpenVPN | WireGuard’s own protocol |
| Security | Good | Very good |
| Speed | Average | Fast |
| Compatibility | Wide | Limited |
| Configuration | Moderate | Easy |
| Logging | May keep connection logs | Minimal logging |
Conclusion
By using “Stealth” VPN encryption, you can easily get through most firewalls, including those that use advanced data packet inspection techniques to recognize and block the VPN traffic. As we’ve discussed earlier, you can use it when you are concerned about your data privacy and the internet regulations of your state.